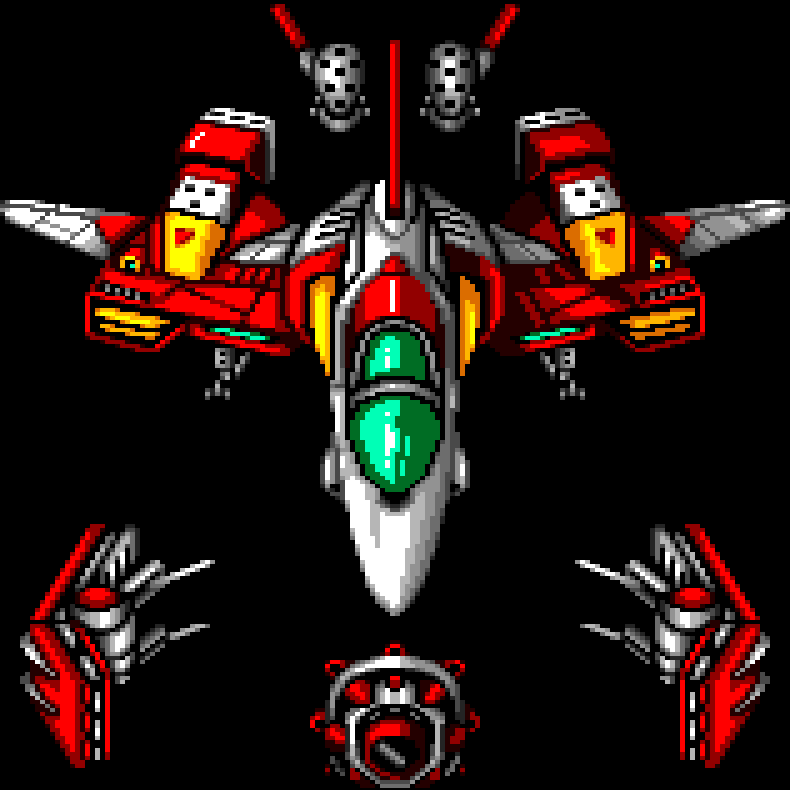
Edit: @Successful_Try543@feddit.org solved it. It says “one special character”. Not “at least one”.
It’s fucking insane that an internet banking portal has such a low cap on max characters and such shitty rule enforcement.
Their desktop site is even more shitty. It won’t allow right click or paste actions. There goes compatibility with password managers.
Bitwarden has a function where it types in (not pastes) the password and shows the prompt for it without right-click.
And even if theres an app for Windows (https://github.com/jlaundry/TypeClipboard) that can type it for you and even has a shortcut.
I am sure someone in the linux world knows an equivalent tool.
We use it at work to paste long passwords when remoting in.On Mac you can use Hammerspoon and just create a shortcut to
hs.eventtap.keyStrokes(hs.pasteboard.getContents())
As a super secret dev hack may I introduce you to
shift + inserta fair few sites specifically blockctrl + vinstead of properly disabling the clipboard action and, of course, if you read this and then submit a Jira ticket to blockshift + insert… well… h8uYou can also drag the password in from another text field instead of pasting
I usually to in the developer tools and manually disable the thing preventing the paste action. It’s usually a string to remove some JS or something or an Event that you need to uncheck
If you’re opening up the dev tools you can also paste your string directly into
<input value="" />unless something weird is going on.*Laughs in blazor*
Aah… I completely forgot about that. Will try next time. Also yesterday I saw Shift + F10 will show the context menu. Yet to test it on this site.
Any password manager should be able to “type in” the password. Or be a browser plugin that doesn’t rely on copy pasting, but use other mechanisms to inject it directly into the field.
But yes, if that’s their online portal, I am not kidding I would change banks.
My bank’s password used to have to be exactly 6 characters, no special characters and you could use numbers and letters interchangeably because it was also your phone banking password.
a previous bank used to have a max password length of 8 characters, then proudly announced that they will increase it to 32
Then I made a typo at the end of my password and it let me in anyway, and I realised they were just trimming the first 8 characters to give the illusion of security
That is so insane. To think they would rather just clip the passwords instead of habing it be longer.
Did you try out your hypothesis by using the first 8 letters than just random junk until you hit your password length?
I tried then first N characters of my password until I found out the threshold was at 8, then I tried with the first 8 chartacters of my password and then random junk and it worked.
I also had two friends in the same bank to validate
Unbelievable.
And I’m honestly surprised they let you do that many password tries. I would seriously consider changing banks.
Visa has a hard limit of 8 and requires the first 4 to be numbers because the phone tree might require it as a password
The whole banking industry is ridiculous and is ridiculously legislated
USAA has 8-12 ONLY. My smallest memorized password algorithm is 13 characters, that I typically use for throwaways, doesn’t even fit.
The ERP software I have to use has a strict limit of 6 characters as password. Only alphabet and numbers allowed.
Maybe when I leave I try an SQL injection.
Bobby tables, noooooooo!
I had to create an account on a government website. The website didn’t list a character limit so I used a password manager to generate a 32 character password. My account was created but I couldn’t log in. I used the “forgot my password” option and I received an email of my password in plain text. I also noticed why I couldn’t log in. The password was truncated to just 20 characters. Brilliant website! Tax dollars at work!
Some internet banking sites give access after only asking for login password. They will only ask for transaction password and OTP (that will only come on phone) later on. Asking for two passwords isn’t necessarily more secure since many people will just reuse their original one again. And OTP instead of offering something like hardware security key is insane.
My bank uses 6 digit ‘customer number’ (which is set by the bank) and that’s verified with an app and a personal PIN (app shows ‘login attempt ABCD at mm.dd. hh:mm’ where ABCD is shown on login page too) or via SMS OTP (again with ‘ABCD’ verification). And again with personal pin + app or OTP to confirm transactions. The app itself can be protected with a fingerprint or phone pin and every new installation needs to be registered to the system, so I can’t just use my phone app to access my wifes account (or anyone elses) but I still can map multiple accounts (like corporate ones) to the same installation.
I think that’s pretty reasonable approach.
Reason why I took a hardware tan generator versus using the OTP function of one of their other apps.
Thanks but no, I will use the old crusty method as I know how easy that’s hacked.
They can’t even properly check their copy on critical infrastructure. Top notch work over there, top to bottom.
seriously, I’ve never seen a bank with password login to begin with. Every bank i know of uses physical devices that you type a code into
Never heard of this. Where is this at? :o
Sweden. The little keyfob thingies have been the thing for many decades here, I would guess ever since the dawn of internet banking, but I’d have to ask my parents instead of just assuming. I used to assume that was just normal for banks in the world at large. When you want to log in, the website gives you a code, you type the code into the fob and it responds with another code you type in to the website.
Nowadays they additionally offer login via BankID, a mobile app used throughout Sweden for personal online identification.
As a German, when living in Sweden, I was (and still am) very impressed, how widespread the use of (Mobile) Bank ID, beside the use of the personal ID number (As a male German, the state has assigned me at least three different ones without requiring any interaction.) for basically everything, is.
In Germany, before introducing a second electronic way of authentication for online (or phone) banking, it was done by a chosen password and a TAN (transaction number) from a list that you regularly got sent by mail in a special envelope. Later it was replaced by that “thingy”, a mobile TAN generator, or push TAN via SMS.
OMG the special envelope seems to make it specially easier for people to steal just the right mail
It was not special from the outside, but from the inside. It was either the envelope or the TAN list that was printed with a special pattern to prevent reading the list by using a flashlight.
I want this so bad now.
OTP for 2FA has just started becoming common here (US) within the last decade I think. Each bank has its own separate app and many banks seem to limit password lengths to less than other websites.
It is insane that any internet banking portal still uses a static password.
At least it should not, in many countries must not, be the only measure.
I once encountered an OR in the requirements: Capital letters, small letters and digits OR special characters.
It says one special character, not at least one. Maybe the password has more than one.
Holy shit!! You did it. I would never expect a banking password to max special characters. I have been scratching my head with Bitwarden and this shitty app for an hour.
But wouldn’t that mean the bottom checkbox should be cleared and the 2nd one should be checked?
Still doesn’t make sense.
Yeah that’s true. The UI does not accurately represent the validation conditions.
Yes, the 2nd one implies that there should be more than one.
And the wording is fucking terrible as well
i have to wonder if banks actively don’t want us to use them
It’s like a Captcha that only lets in autistic people.
You solved the puzzle! here is a cookie for you :D 🍪
Yay!
Good catch.
Also psh, there’s no verb, suggesting the password should be exactly one special character and nothing else.
I love how the acceptance/rejection status is messed up.
If it’s only one special character, then that should be unchecked not check, and the combination of “letters, numbers and special characters” should be check marked.
That programmer has obviously been playing https://neal.fun/password-game/
I remember seeing the most optimal password for this game but now I can’t find it
problem is the late stages of the game the password requirements change when your password’s emojis start catching fire.
I put that out but the stupid chicken choked while I was looking for a YouTube video 4:42 long
I can never get past the geoguesser part
Last time I got pretty deep in, but it became impossible when the chess notation rule required Cs and Ds, making it impossible to stay below the roman numberal sum limit.
deleted by creator
I used Google lens. Got stuck afterwards on a chess rule. The captcha rule used the notation for the chess one to complicate it further haha
I got past it because it happened to throw a place from my country. And there was also a flagpole with a flag on it to really drive it home. XD
It says “one special character”. Not “at least one”.
oh. oh god. what the fuck.
No Homers.
If >1 special character is not allowed the last check should be failed . The second check is literally satisfied even if there are 2+ specials.
I’d not be using that bank.
Now imagine how many services just silently cut off your password at 8 characters and people never notice.
UltraVNC is very guilty of this.
Wells Fargo cuts to 14 on their sign in page but not on their change password page, ask me how I know
Once upon a time, battle.net passwords weren’t case sensitive. I used upper and lower case letters in my password then one day realized I didn’t hit shift for one of the caps as I hit enter out of habit, but then it still let me in instead of asking for the password again.
It was disappointing because it takes more work to remove case-sensitivity than to leave it. I can’t think of any good reason to remove it. At least the character limit had a technical reason behind it: having a set size for fields means your database can be more efficient. Better to use the size of a hash and not store the password in plaintext, so it’s not a good reason, but at least it’s a reason.
It’s possible that the passwords want through an old ass cobalt system or something that forced everything to be capitalized so to solve that they made everything non case sensitive.
But even that sounds insane as the passwords should have been hashed.
COBOL
What if they got hashed by that cobalt system :P
At least the character limit had a technical reason behind it: having a set size for fields means your database can be more efficient.
If that is the actual technical reason behind it, that is a huge red flag. When you hash a password, the hash is a fixed size. The size of the original password does not matter, because it should not be stored anyway.
Correct, hence the sentence after the one you quoted :)
If any service can recover your password and send it back to you rather than just resetting it for you to set a new one, don’t rely on that service for anything you want to keep secure. And certainly don’t reuse a password there, though you shouldn’t be reusing passwords anyways because who knows what they are and aren’t storing, even if they don’t offer password recovery.
Sorry, didn’t want this to look like an attack or disagreement. Just wanted to highlight that point, because arbitrary maximum sizes for passwords are a pet peeve of mine.
Yeah no worries and agreed. I hate seeing commercial sites using worse password sanitization practices than I used for my first development website that wasn’t even really intended for anyone else to log in to and any max length suggests the password is either stored or processed in plaintext.
IMO it should even be hashed on the client side before being sent so that it doesn’t show up as plaintext in any http requests or logs. Then salted and hashed again server side before being stored (or checked for login).
IMO it should even be hashed on the client side before being sent so that it doesn’t show up as plaintext in any http requests or logs. Then salted and hashed again server side before being stored (or checked for login).
But if someone got that hashed version they could hack the client to have client side hashing code just send that hashed value to the server. You’d want to have the server to send a rotating token of some sort to use for encrypting the password on the client and then validate it on the server side that it was encrypted with the same token the server sent.
Seems complicated to me… https is probably has good enough encryption, so eh, whatever.
Yeah, if they are able to intercept traffic or access the logs, they probably already have other access to the account without needing the password. If you don’t reuse passwords, then your other accounts will be safe from that.
Your Internet Banking Password should one special character (~!@#%^&*)
Great grammar on their part.
Yeah, they noticed their mistake too late, hence the expletive.
atleast a 5/10 in effort
 This broke me. 🤣
This broke me. 🤣
Maybe you accidentally did a permutation instead of a combination.
This was a new one for me:
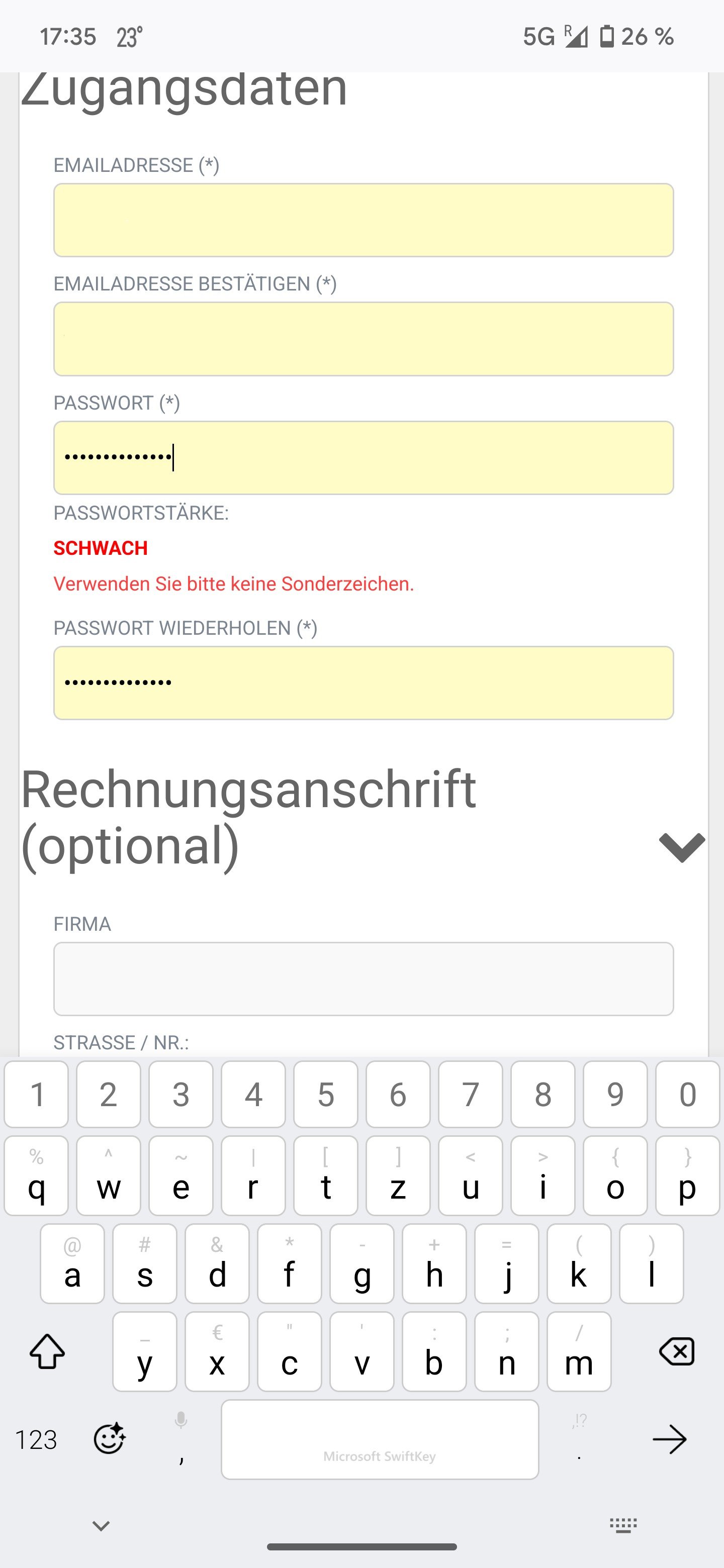
Translation: Password strength: weak. Please don’t use any special characters.
It was a generated 14 char password… (╯°□°)╯︵ ┻━┻)
I used to use a system that was perfectly happy to let you use a semicolon when setting the password, but then login would fail if you did.
When you enter an apostrophe, and the site returns a 500 response stating you are trying to attack it. (And yeah, it’s always 500, not 400.)
Noone should of aloud this code to go out the door. Atleast alot of other people people probably complained aswell, so your apart of a bigger group, incase you were worried.
spoiler
And yes, this was painful to type.
I miss Allie’s blog alot.
Your comment is painful to read.
Your well come.
My guess is they mean, one capital letter, one lower case letter, a number, and a special character
what’s always amused me about these rules is that they exist because people are dumb. Technically, they lower the difficulty of the passwords slightly. ( for example, knowning that one character is a number reduces it to 10 options in stead of 10+26+26+whatever set of special characters)
anyhow. people should use password managers. just saying.
Please tell me someone didn’t buy software with ‘atleast’ spelled like that in there. Please, tell me someone tested the web app and had the brains God gave a douglas fir and knew that wasn’t a word; that it was never a word; that the writer’s spell check should have picked that up; that it’s not been over-ruled by stupid so much that it just takes it.
Well now. When we’ve been enforcing password requirements at work, we’ve had to enforce a bizarre combination of “you must have a certain level of complexity”, but also, “you must be slightly vague about what the requirements actually are, because otherwise it lets an attacker tune a dictionary attack against you”. Which just strikes me as a way to piss off our users, but security team say it’s a requirement, therefore, it’s a requirement, no arguing.
“One” special character is crazy; I’d have guessed that was a catch-all for the other strange password requirements:
- can’t have the same character more than twice in a row
- can’t be one of the ten-thousand most popular passwords (which is mostly a big list of swears in russian)
- all whitespace must be condensed into a single character before checking against the other rules
We’ve had customers’ own security teams asking us if we can enforce “no right click” / “no autocomplete” to stop their users in-house doing such things; I’ve been trying to push back on that as a security misfeature, but you can’t question the cult thinking.
Why do they think no copy paste is safer?
Because if you disable browser autocomplete, what’s obviously going to happen is that everyone will have a text file open with every single one of their passwords in so that they can copy-paste them in. So prevent that. But what happens if you prevent that is that everyone will choose terrible, weak passwords instead. Something like
September2025!probably meets the ‘complexity’ requirement…